NIS-2 Compliance, we get you from A to C!
What does NIS-2 stand for?
NIS-2 Directive
The NIS-2 Directive stipulates the cyber and information security
of companies and institutions. It states that EU
member states must transpose the contents of the Directive
into national law with corresponding legislation by October 2024.
The NIS-2 Directive changes / supplements the BSI Act, where it
extends the sectors through the additional assessment
of the impact on particularly critical facilities and important
facilities. On 7 May 2024, the Federal Ministry of the Interior
published the draft bill for the NIS-2-UmsuCG
(NIS-2-Umsetzungs- und Cybersicherheitsstärkungsgesetz) in Germany.
Once the NIS-2-UmsuCG comes into effect in Oct 2024, compliance in
companies will be monitored and sanctions will be imposed in the event
of violations!
Note: ISO 27001 certified companies have a sound foundation for achieving NIS-2 compliance!

Who is affected and how is it determined?
According to NIS-2 UmsuCG § 28 - Particularly critical facilities and important facilities, the impact is categorised using threshold values:
Companys
Sectors
Employees
Revenue
Balance
Particularly critical facilities
NIS-2 UmsuCG Annex 1
a) > 250
b)
> 50 Mio. EUR
43 Mio. EUR
Important facilities
NIS-2 UmsuCG Annex 2
a) > 50
b)
> 10 Mio. EUR
13 Mio. EUR
Who is responsible for NIS-2 implementation
within affected companies?
According to the NIS-2 Directive, the Liability situation for management bodies of critical and important organisations is regulated as follows: NIS-2 Directive
CHAPTER IV - RISK MANAGEMENT MEASURES AND REPORTING OBLIGATIONS IN THE FIELD OF CYBER SAFETY (NIS-2 Directive)
Clause § 20 - Governance
- Member States shall ensure that the management bodies of
critical and important organisations approve the cybersecurity risk
management measures taken by those organisations to comply with Article
21, supervise their implementation and are held accountable for violations
of this Article.
The application of this clause will not affect national law in relation to the liability rules applicable to public sector organisations and the liability of public officials and elected or appointed officials. - Member States shall ensure that members of the management bodies of critical and important organisations are required to participate in training and shall require critical and important organisations to provide regular training to all employees in order to acquire sufficient knowledge and skills to identify and assess risks as well as management practices in the context of cybersecurity and its impact on the services provided by the organisation.
The NIS-2 Implementation and Cyber Security Strengthening Act, Chapter 2 - Risk Management, Reporting, Registration, Verification and Disclosure Obligations of the NIS-2 UmsuCG requires the following of the executive boards of critical facilities and important facilities:
Clause§ 38 Duty of authorisation, supervision and training for management boards of particularly critical facilities and important organisations
- Executive boards of particularly critical institutions and important institutions are responsible for authorising the cybersecurity risk management measures to be taken by these institutions in accordance with § 30 and for supervising their implementation.
- A relinquishment by the institution of claims for compensation due to a violation of the responsibilities under paragraph 1 or a settlement by the institution of these claims that is grossly disproportionate to an existing uncertainty about the legal obligation is invalid. This shall not apply if the party obliged to pay compensation is unable to pay and makes a settlement with its creditors to avert insolvency procedures or if the obligation to pay compensation is regulated in an insolvency plan.
- The executive boards of particularly critical facilities and important facilities must attend regular training to acquire sufficient knowledge and skills to recognize and assess risks as well as to develop risk management practices in the area of information technology security and to understand the impact of risks and risk management practices on the services provided by the facility.
What steps should you take if your company has been assessed as being affected by NIS-2?
According to NIS-2 UmsuCG , Chapter 3 - Risk management obligations, disclosure obligations, Obligation to provide proof and Obligation to provide information, §§30ff, there is an obligation for affected companies to implement a risk management system, an obligation to register and an obligation to comply with reporting channels.
Which minimum requirements must be met for NIS-2 implementation?
- Concepts relating to risk analysis and security of information technology,
- Management of security incidents,
- Business continuity management, such as backup management and disaster recovery, and crisis management,
- Security of the supply chain, including security-related aspects of relationships between individual organisations and their immediate suppliers or service providers,
- Security measures for the acquisition, development and maintenance of IT systems, components and processes, including management and disclosure of vulnerabilities,
- Concepts and procedures for evaluating the effectiveness of risk management measures in the context of information technology security,
- Basic cyber hygiene procedures and information technology security training,
- Concepts and procedures for the use of cryptography and encryption,
- Security of personnel, concepts for access control and for the management of systems,
- Use of multi-factor authentication or continuous authentication solutions,
- Secure voice, video and text communication and, if necessary, secure emergency communication systems within the facility.
How we can provide you with professional support:
- We support you with the required registration of your company and the operationalization of the necessary reporting channels!
- We support you in carrying out your GAP analysis!
- We plan and support your ISMS transformation project with the aim of collaborating to document and operationalize the necessary guidelines, processes and procedure instructions in compliance with NIS-2!
- We help you strengthen your supplier management with a focus on the security of your supply chain!
- We provide support in operationalizing the relevant business processes!
- We review the maturity level of your NIS-2 ISMS through internal audits and assist you with any necessary optimisations!
- We assist and accompany your company during your ISO 27001 certification or re-certification process!
- We complement your existing capabilities with SOCurity Services (SOC as a Service)!
- We help guide you with a comprehensive incident management service!
Today’s cyber security landscape is complex. SAMA PARTNERS offers strategic security guidance and solutions to organisations across the globe to navigate this complexity.
We help you at every stage of your security journey to identify your needs, set your security journey, assess and test your defences, and select the solutions that match your security needs - whether that requires building an entirely new security strategy or upgrading your protections to combat the latest threats and trends.
SAMA PARTNERS combines its cutting-edge consulting and expert services with security operations services on your behalf: beginning by consulting through capacity enhancing through staffing and training to complete take over your security operations in our dedicated 24/7 Security operations Centre (SOC).
SAMA PARTNERS is your sparring partner that offers services covering the whole lifecycle of security journey.
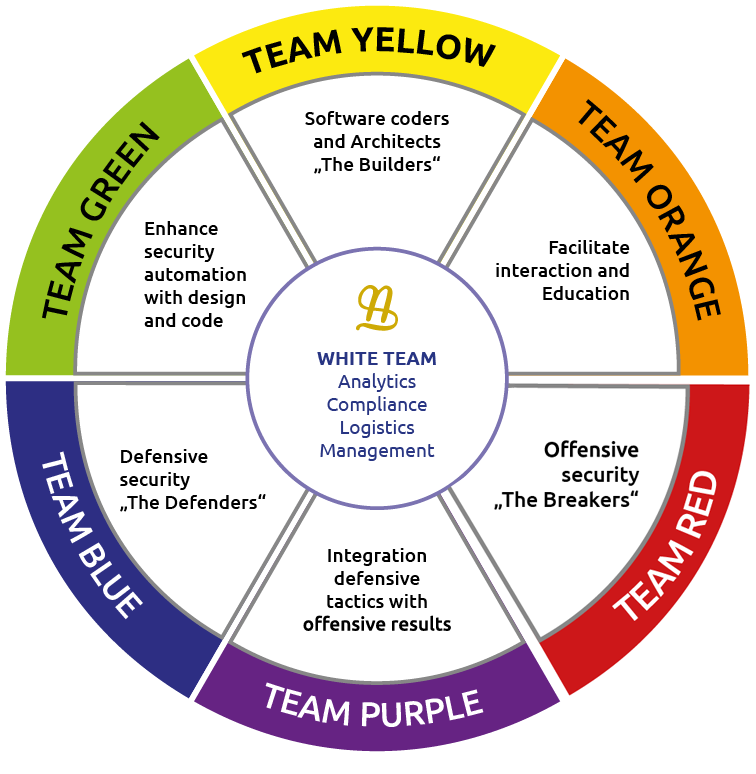
SAMA PARTNERS masters both defensive and offensive security. Our consultants are both subject matter experts and security specialists. We are organized along different specialty fields and teams ensuring our customers a wide range of expertise and radius of action.
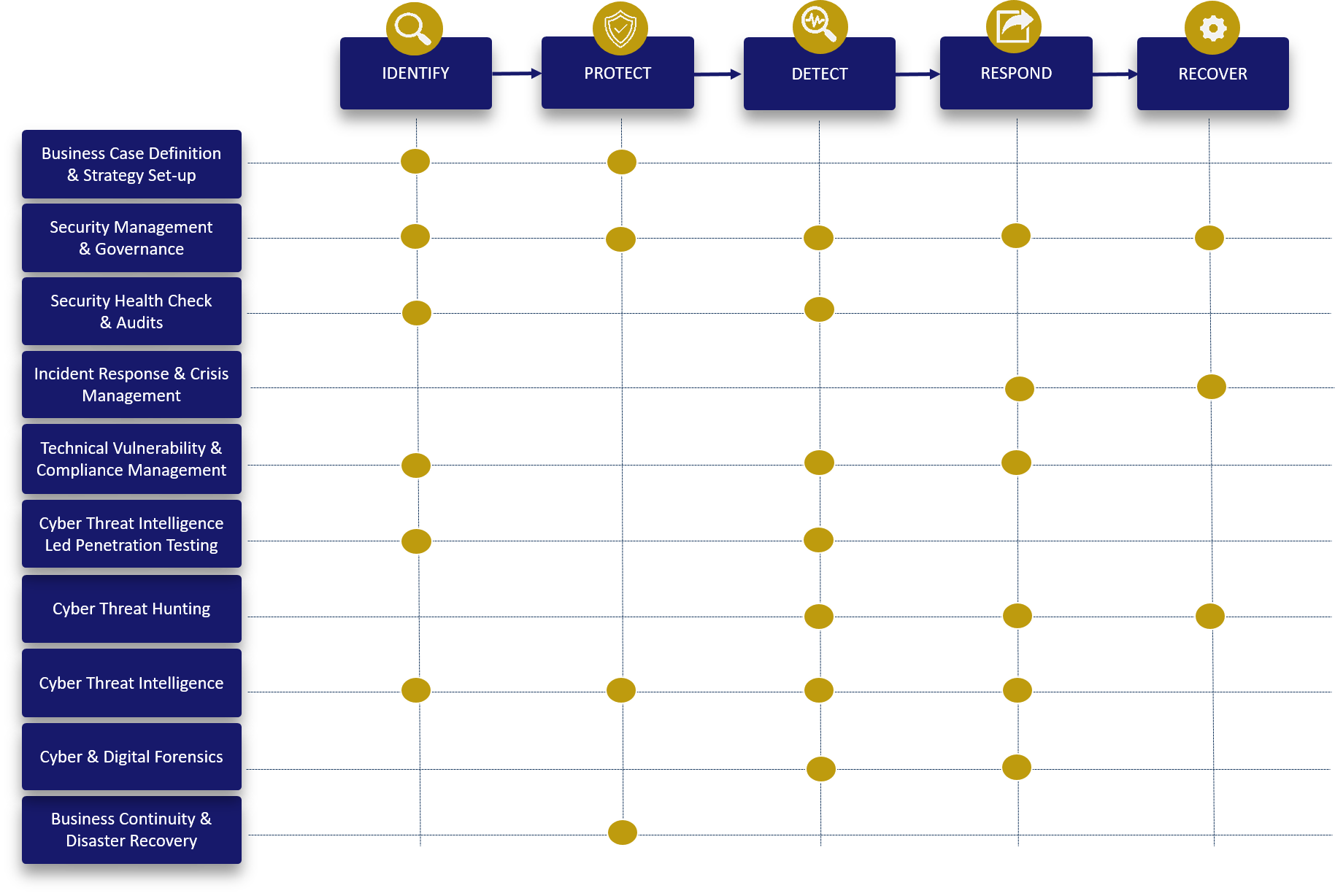
SAMA PARTNERS Sphere of Knowledge
Business Case Definition
& Strategy Set-up
Business leaders and security managers are standing at a critical
crossroads in the face of rising information and cyber risks.
In the ever-growing reliance on digital world, the business
resilience of any company depends hugely on its cyber and
information resilience.
SAMA PARTNERS assists business leaders and decision makers to rethink and assess their cyber risks and make it an organizational priority. SAMA PARTNERS exhausts its experience in different industry sectors, it's up to date knowledge about security relevant legal and compliance requirements associated to each sector, as well as it's outstanding insights into the existing and evolving threat landscape, to provide its customers with a 360 degree view into their right-scaled business needs for information and cyber security and to align the security expenditure with these needs.
SAMA PARTNERS defines with you your business case for information security and provides you seamless strategies and working plans to efficiently and cost-effectively achieve the goals.In doing this, SAMA PARTNERS helps you to identify the needed resources for your security program, introduce and integrate information security management processes and to choose the best technological assistance to enhance your defence capabilities and to better embrace and handle risks.
Your cyber security strategy should be proactive, effective, actively sustained and scalable.
We frame your needs for cyber and information security and help you align your activities with these needs to maximize your ROI and reduce risks.
Our Security Management & Governance
All companies, including very small businesses, must organize their
governance to ensure their cyber resilience.
Indeed, the increase of cyber attacks goes beyond the expert's
responsibility and must become a corporate project involving all
stakeholders, and especially human resources. Cyber resilience
transforms the expert model into a risk management model.
SAMA PARTNERS Security & Compliance approach is to efficiently
bring security up to the start of the information system lifecycle,
build heat-resistant architecture architecture to enable information
security, and to create the foundations for fulfilling compliance
requirements.
Based on our security core competence (IT, information security and
cybersecurity), SAMA PARTNERS pursues an integrative approach in
order to link the areas of classical IT (from softwaredevelopment to
IT service management) with the business processes and, at the same
time, to meet the requirements of operational and industrial IT.
Information Security
Information security is indispensable. As a component of corporate
management, it must be geared to providing optimum support for
business objectives.
The growing complexity of cyber-threats as well as the rising number
of legal and business requirements makes a structured approach to
managing the security organisation and processes within a company an
imperative.
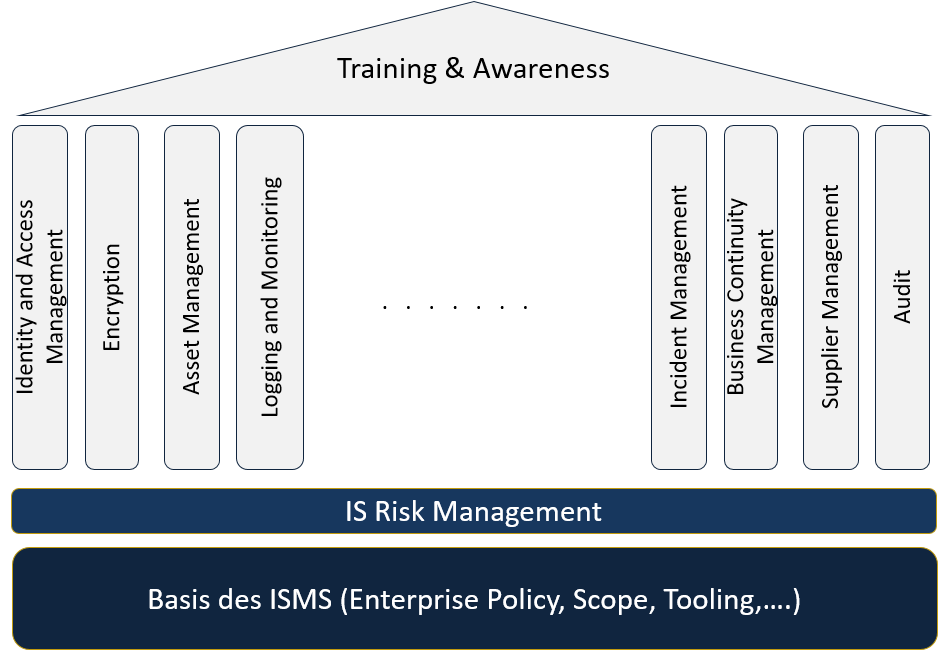
An information security management system (ISMS) in accordance with
internationally standards offers the optimal basis for the efficient
and effective implementation of a holistic security strategy. A
healthy and continually improving information security management
system (ISMS) helps mitigating risks. Ensuring that your ISMS is
tailored to your organization and corresponds to international
standards may require the guidance and advice of experts in the
field.
Our security architects and experts will collaborate closely with
you to create truly customized ISMS and find innovative solutions to
your particular security challenges. We promise you a solid
construction of your ISMS that not only success any audit, but also
and especially add value to enable you to govern your security
processes and challenges.
We envision a future without cyber risks, where the likelihood and the impact of a cyber attack is minimized to the point where risk is essentially zero.
Security Health Check & Audits
Whether you want to establish security practices from scratch or just intend to foster existing controls, you need to consider conducting a health check for your security organisation.
Auditing the health and performance of organizational controls is an essential component of successful security management systems. Audits may also be used to raise awareness and identify existing control weaknesses in security.
Depending on the needs of your organization, several standards and best practices could be used to conduct the health check.
In addition, this can be done by reviewing individual organizational regulations as well as selected measure objectives of for example ISO/IEC 27001 or TISAX. The main components of organizational security health check & audit are policy-making, organization, planning, performance measurement and review, which provide the environment in which effective auditing systems operate.
Technical health checks aim to assess the efficiency and the effectiveness of IT systems.
Our consultants cover both the technical and strategic aspects of information security management systems during the course of the information security analysis service delivery. Throughout an engagement, we focus on granular knowledge exchange with you to deliver a comprehensive report containing the assessment findings, any identified weaknesses, detailed remediation measures, as well as risk probability and impact assessments.
We will provide you with assistance to:
• Understand your threat landscape.
• Assess your organization's ability to identify and deal with the
cyber risks.
• Assess your security maturity.
• Find out how to improve your security plan.
• Develop and deploy security processes based on risks and controls
issues and matching your business.
We can no longer simply wonder if our businesses will be affected, but rather, WHEN and HOW FREQUENTLY these attacks will occur.
Times are changing, so is cybercrime.
Be willing to reassess your cybersecurity approach considering the
new threat industries!
Incident Response
More than 70% of organizations do not have an incident response plan in place.
Several attacks are opportunistic and will not target you directly. Instead, attackers will test all doors and open or force open those that are not securely protected.. A cyber incident is an unauthorized attempt, successful or not, to gain access to a system resource or computer system, or to modify, destroy, delete or make it unavailable.
Security Incident Management involves incident monitoring, reporting, impact assessment, incident escalation and post incident review. SOCurity® incident team is responsible for analyzing and handling the security threats and impact of information security incidents and to drive the process as efficiently as possible.
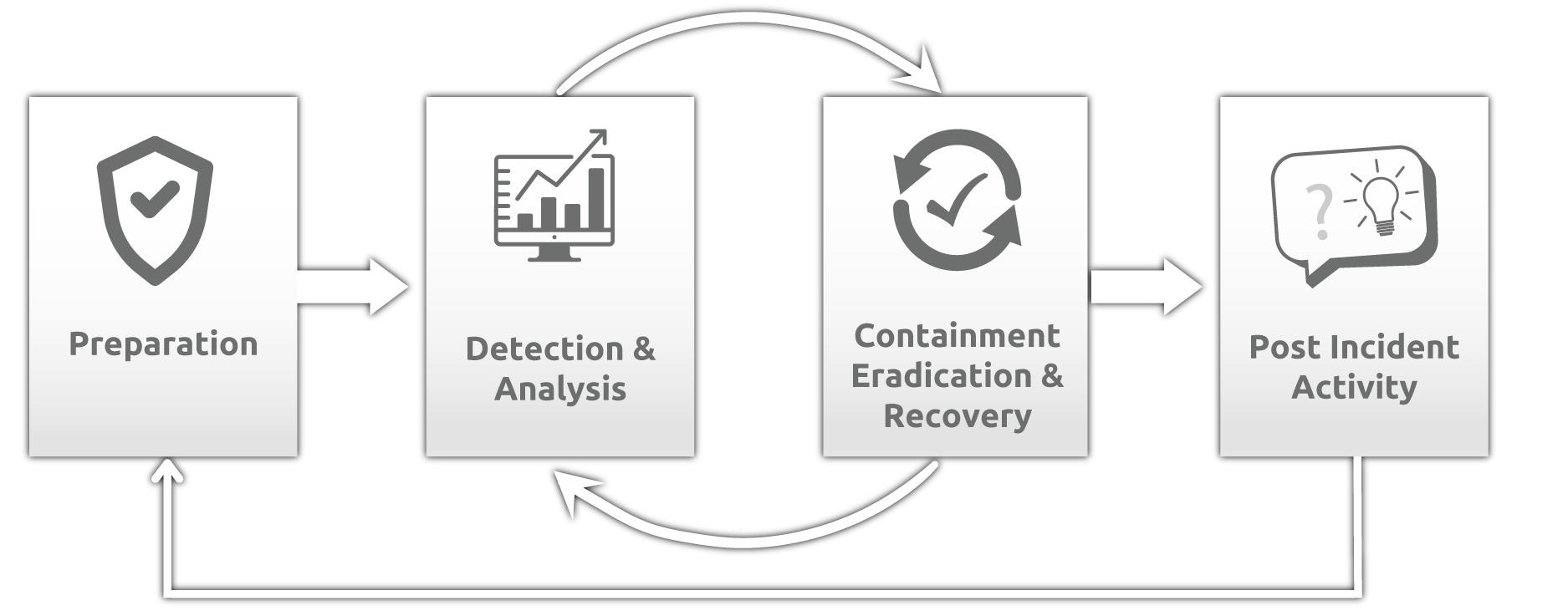
Incident Response Readiness
Crisis Management
The explosive growth of attack sources and tactics should lead
companies to organize themselves. Even they have already a
traditional crisis management, they have to integrate the cyber
dimension and review their organization, processes in their crisis
management strategy.
Facing such an attack requires companies to implement a certain
number of additional specific measures (SOC and CERT, external
partners, detection and protection tools...) which will be
determining factors in ensuring effective crisis management.
The crisis management aspect of an incident is very important,
even critical. This includes having the right players around the
table depending on the level of criticality and complexity, but
also communicating the information correctly inside and possibly
outside the organization.
Technical Vulnerability Management & Compliance
With the arising complexity of digital world, attack surfaces and
the number of bad actors grow in scope and scale every day. The
number of security defects, weaknesses and vulnerabilities increase
daily, it can be difficult to manage 100% of your exposure to
risk.
SAMA PARTNERS takes a risk-based approach towards technical
vulnerability management (TVM). discover the critical assets, and
threats and vulnerabilities relevant to any organization.
SAMA PARTNERS uses a near real-time vulnerability platform to
display the scan results. The platform allows you to communicate,
collaborate, and manage your vulnerability program in a centralized
manner. It maps your vulnerabilities to known threats and context
and assigns a risk rating for assets that stand exposed.
The compliance management program makes use of the so-called CIS
Benchmarks to provide the baseline configurations and to ensure
compliance with industry-agreed cybersecurity standards. Our
services also cover several compliance proofing scans such as PCI
DSS scans.
Our TVM experts will help you offload day-to-day operations by
providing the granular focus each vulnerability demands. SAMA
PARTNERS helps extend coverage across your entire attack surface so
your TVM program can run more holistically.
Whether a scheduled monthly scan, a validation scan, or just an ad
hoc scan as a reaction of an arising critical vulnerability, our
experts will be at your side to reduce the time of detection and
timely begin with remediation steps.
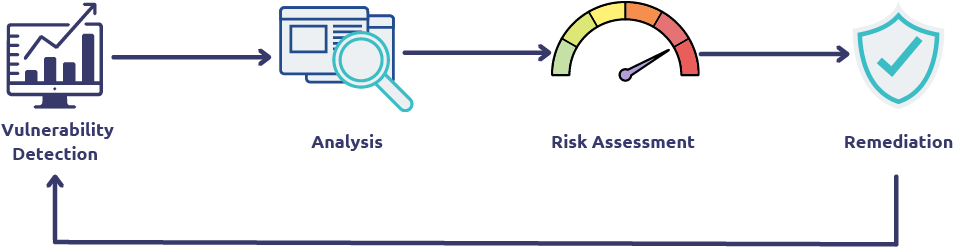
SAMA PARTNERS Security Vulnerability Assessment
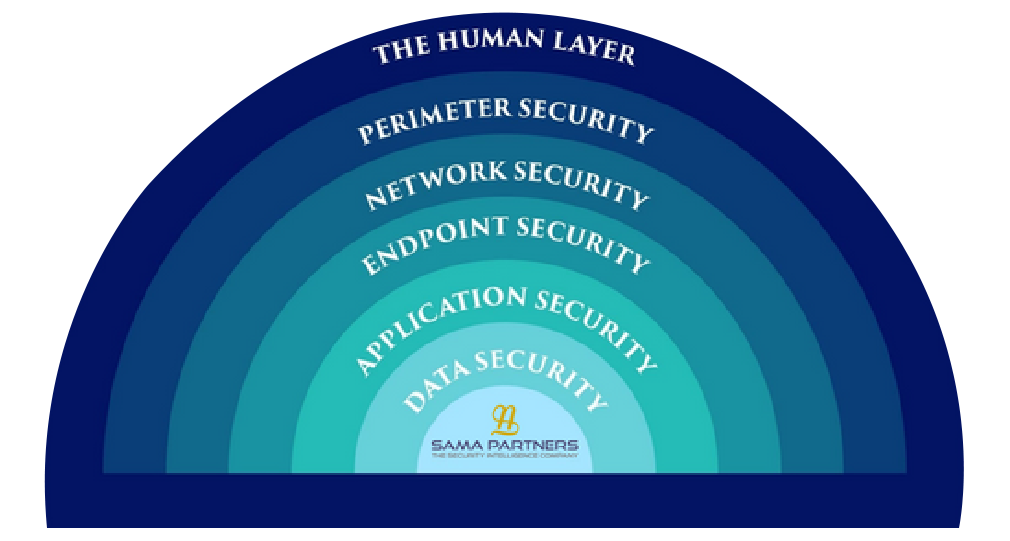
Layered Security with SAMA PARTNERS
Cyber Intelligence Led Pentesting for a Proactive Security Posture
Besides the classical penetration testing, SAMA PARTNERS established
a cyber threat intelligence-led penetration testing approach.
Traditional penetration testing may lack real-world context and can
be less applicable to combating actual threat actors.
The CILP approach significantly improves the value of penetration
testing by utilising the latest threat intelligence and ensuring
that it is tied to the business context of a customer. It helps the
penetration testers to get an “attacker’s perspective” about your
organization’s infrastructure: what they see, how to get in, and the
critical targets.
SAMA PARTNERS testing team uses cyber threat intelligence to emulate
the tactics, techniques, and procedures (TTPs) of an adversary
against target systems in real-time.
SAMA PARTNERS' cyber threat intelligence service provides the
penetration testers with the most accurate and actionable threat
intelligence information.
Our Red Teams in Security Testing Vulnerability Assessment, Pentesting & Attack Simulation
SAMA PARTNERS' intelligence-led red team testing involves the use of a variety of techniques to simulate an attack. It follows a rigorous procedure: Reconnaissance, Information Analysis, Execution, Exploitation, Control & Movement, and Actions on Target. Vulnerability Assessment, Pentesting, and Red Teaming are commonly used by SAMA PARTNERS interchangeably and according to our clients needs. SAMA PARTNERS Vulnerability Assessment is a solid systematic examination of your information systems or products that determine the adequacy of your security measures and identify security deficiencies. We focus on finding vulnerabilities and prioritizing them by risk.
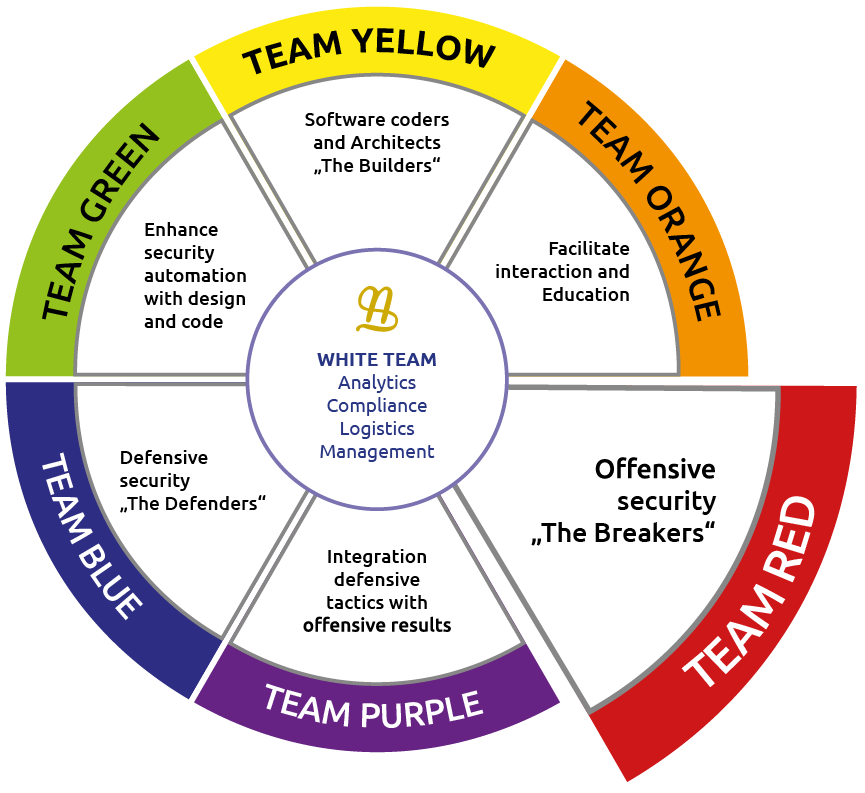
SAMA PARTNERS sphere of knowledge
We merge Threat Intelligence, Skills and Technologies for a Proactive Security Posture!
Cyber Threat Hunting
Our Cyber threat hunting approcach is based on a proactive security search through networks, endpoints, and datasets to hunt malicious, suspicious, or risky activities that have evaded detection by existing tools. Threat detection is a somewhat passive approach to monitoring data and systems for potential security issues, but it’s still a necessity and can aid a threat hunter. Proactive cyber threat hunting tactics have evolved to use new threat intelligence on previously collected data to identify and categorize potential threats in advance of attack.
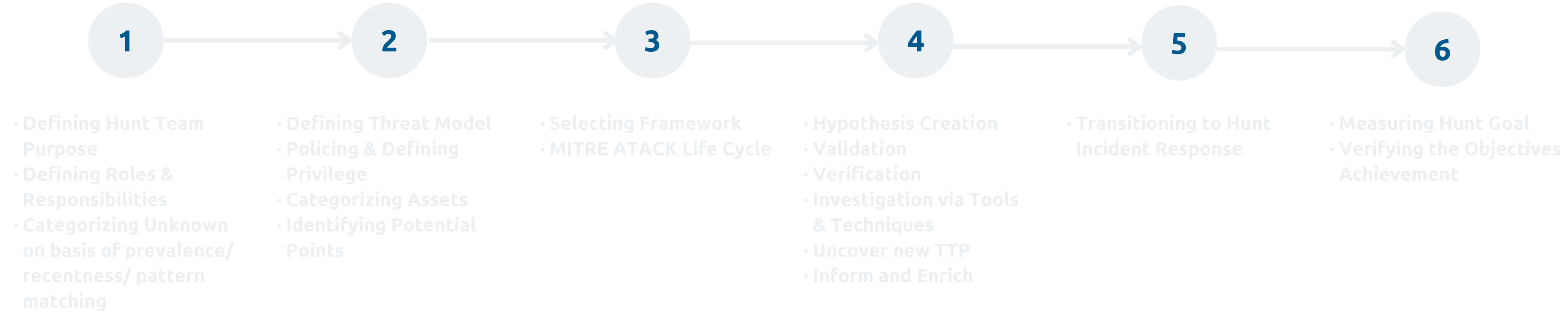
Many organizations are unaware that their confidential data is being compromised by an adversary. This hap-pens because security mechanisms lack proactive search-ing of threats.
Find out
about our Threat Hunting Methodology
Cyber Threat Intelligence
The analysis of an adversary's intent, opportunity, and capability to
do harm is known as cyber threat intelligence (CTI). To optimize its
resources and to provide the needed guidance about the existing threat
landscape and the typical groups acting against its own industry
sector, companies need to adopt intelligence-driven security defence
practices that go beyond preventative technologies and the perimeter,
and beyond events-based monitoring.
SAMA PARTNERS established CTI services that provides its customers
with timely, relevant, customized and actionable information to
enhance their security functions.
SAMA PARTNERS provides human CTI consumers with the right ingredients
and CTI inputs to direct and assist in analysis and response
activities.
Similarly, our CTI service provides your tools with CTI information that serve to sharpen detection and patterning and automate the service:
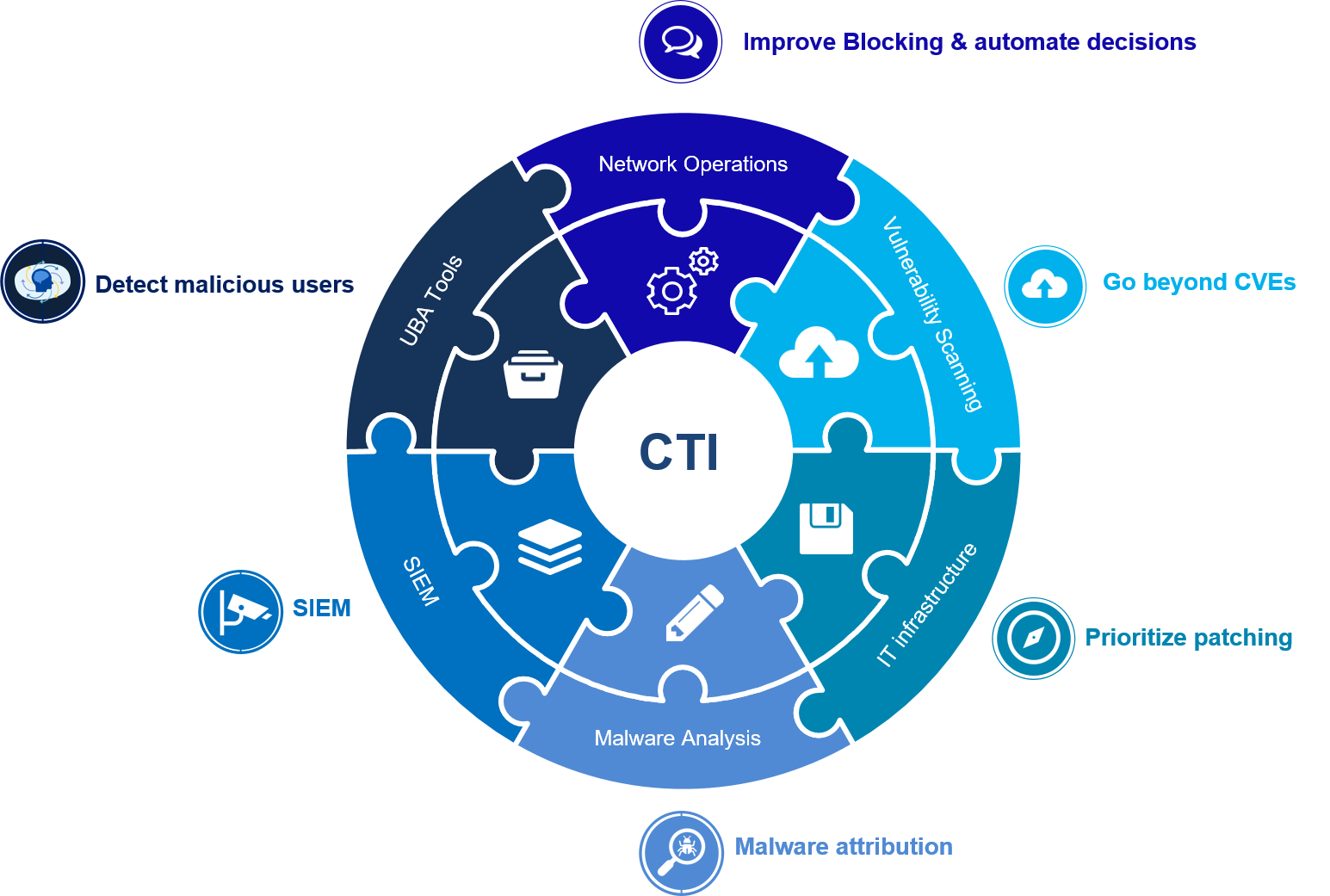
Cyber & Digital Forensics
Situations may arise where only preventing or defending an attack is
no longer sufficient, and that you need to understand what exactly
happened, how it happened and probably also who did it and why.
Almost every crime leaves behind digital data. In order to be
effectively prosecuted in cyberspace, the traces on digital devices
must be traced back to their source and secured.
Cyber and digital forensics services assist you to answer the above
questions and to clarify for you and probably also for your
stakeholders a certain case.
SAMA PARTNERS’ Forensics as a Service assist you to produce digital
evidence of the any cyber or digital attack for legal proceedings or
internal action.
SAMA PARTNERS experts will be your sparring partners to identify
needed data and evidence, to conduct the needed analysis, to
document findings in the form and depth you need for your case.
Have you been the victim of a Cyber Attack?
Our forensics experts investigate and provide you with a report detailing: evolution of the attack, resources compromised, short-term remediation measures to reduce the impact of the attack and medium-term security measures to protect the infrastructure in depth and avoid any future incident.
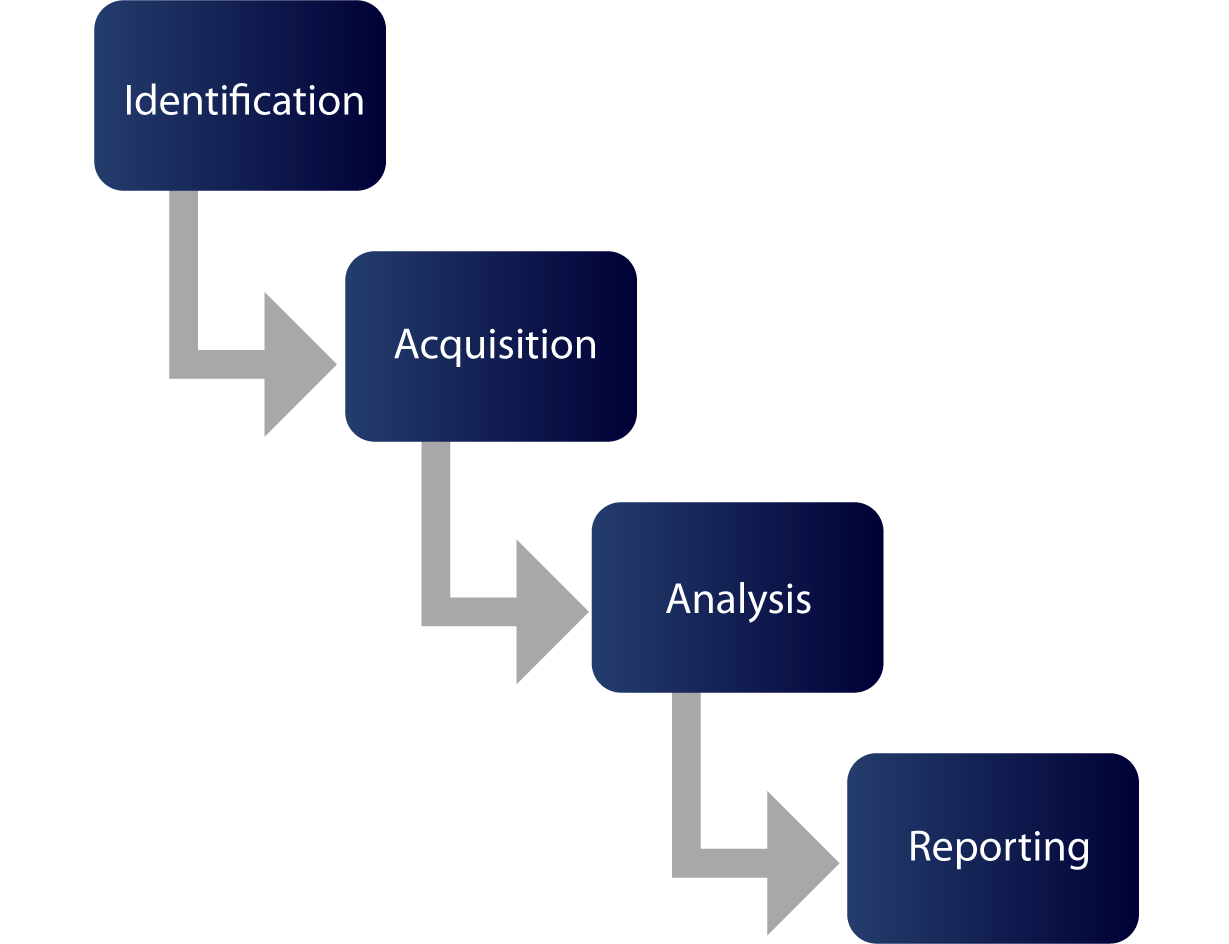
We provide you with the resources you need to quickly and efficiently clarify the causes, paths, and intentions behind every attack, intervene effectively and ensure you the evidence you need for such forensics cases.
Business Continuity & Disaster Recovery
Despite the fact that these attacks can interrupt business operations, many organizations lack an effective business continuity response.
75% of Businesses without a continuity plan will fail within 3 years
after a disaster strikes.
Business processes of a modern organization are increasingly growing
to be reliant on information technology. Therefore, information
security is one of the main concerns of any enterprise, that must
ensure the confidentiality, availability, and integrity of the
organization and its customers’ data. However, news on data breach,
distributed denial of service attacks on different systems occur
daily if not hourly. Even extensive information technology-related
companies are vulnerable to some security issues. It is crucial to
take over information security management as a continuous
process.
Disaster Recovery is often reviewed as the technical aspect of
business continuity and involvement resumption and restoration of
operations.
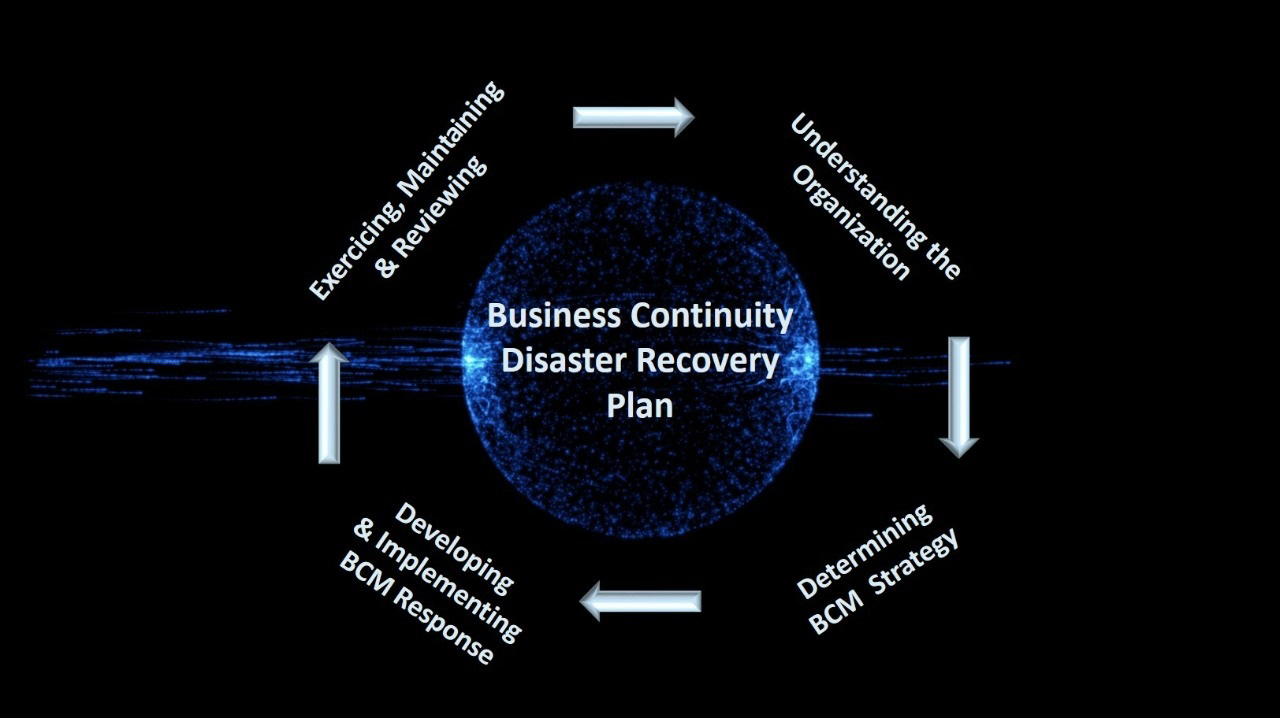
SAMA PARTNERS Business Continuity and Disaster Recovery Approach
To understand why it is important to integrate cybersecurity into the business continuity plan, business continuity planners must first understand the common cyber threats that organizations face and the significant impact of data breaches.
We strive to support and recommend our partners:
- To address the core causes of the disconnect between business continuity and cyber security: the lack of security culture, board support and coordinated response.
- Practical steps to integrate cybersecurity into the business continuity response
- To implement a information management system that enables connection between the organization´s cybersecurity leaders, determining the appropriate response to cyber incidents, assessing the recovery needs and testing the response strategy.
- As employees are often the main point of failure in cybersecurity preparedness, organizations should improve their cybersecurity posture by investing in top-down education and awareness.
CISO-as-a-Service: Your Associate in your Security Journey
Chief information security officers, also known as CISOs, assess, manage and minimize enterprise risks from new and emerging attack surface and emerging threats.
CISO-as-a-Service (CISOaaS) involves outsourcing the role of security leadership and its responsibilities to a third-party provider.
SAMA PARTNERS provides its partners with a reliable and efficient CISO Service. With a CISOaaS, you are primarily outsourcing cybersecurity responsibilities and tasks and assigning them to a qualified specialist with the necessary experience and expertise.
With CISO as a service, you benefit from having access to SAMA PARTNERS’ cybersecurity experts and leaders, on demand, and delegate the work to our security professionals so you can focus on your core business objectives.
Cyber fatigue, or apathy to proactively defending against cyberattacks, affects as much as
42% of companies.
Data Protection
To properly protect data and comply with data protection laws, organisations need both data privacy and data security. Even though these two terms can look similar, their distinctions are clearer once you start to dissect them.
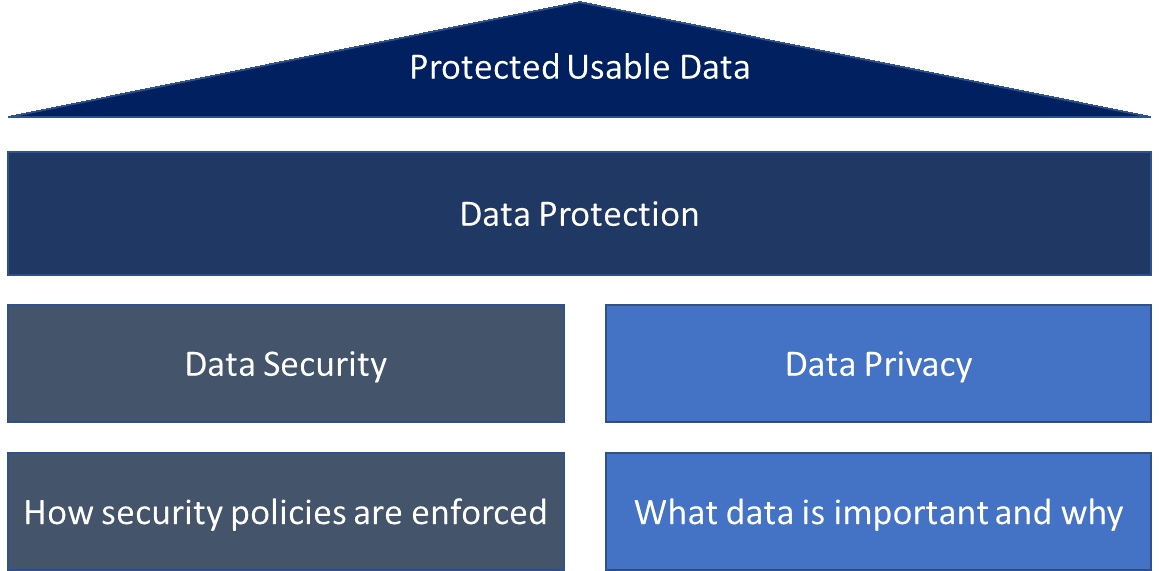
SAMA PARTNERS assists you to identify the requirements for data privacy by focussing on the rights of individuals, the purpose of data collection and processing, privacy preferences, and the way you should govern personal data of individuals.
SAMA PARTNERS also supports you to protect your data from malicious attacks, unauthorized access to digital data, or any intentional or unintentional alteration, deletion, or disclosure of data, and prevents the exploitation of stolen data (data breach or cyber-attack), by identifying and implementing technical and organisational measures (TOMs) to ensure the privacy and security of the data such as access control, encryption or network security.
Security First, Security by Default!
SOC as a Service
Managed services offer all business users prospects for the targeted
further development of their IT.
SAMA PARTNERS established and operates a Security Operations Centre
(SOCurity) to provide its customers with managed cyber security
services 24x7x365. The SOC uses constant monitoring of the IT
infrastructure and preventive measures against cyber threats to
guarantee the availability and security of your company IT assets,
including business-critical applications.
SOCurity offers a variety of security operations services. Our
managed security services comprise several modules that can be
individually combined according to your ideas and needs. This allows
SAMA PARTNERS to respond flexibly to your requirements and provide
you with the level of security you want.
Within SOCurity, our security experts and intelligent tools and
processes will constitute your additional line of defence to achieve
your cyber resilience, around the clock, seven days a week.
SOCurity makes your investments controllable and guarantees you the
maximum return on Investment. You only pay for what you really need,
because our modular SLAs allow SOC services to be adapted to your
needs.
States, multinationals, small and medium-sized businesses,
government organizations, individuals.
No one is safe from the malicious actions of cyber hackers, not even IT specialists!
Find out more about SOCurity
We can no longer simply wonder if our businesses will be affected, but
rather, WHEN and HOW FREQUENTLY these attacks will occur.
This is our new Reality!